In this guide, we will explore how to convert a VMware snapshot into a memory dump. You might wonder why this conversion is necessary. One major reason is forensic or malware analysis.
Some malware resides in memory and leaves no traces on disk. Malware analysts often use memory dumps to identify malicious code or processes present in memory at the time of the snapshot.
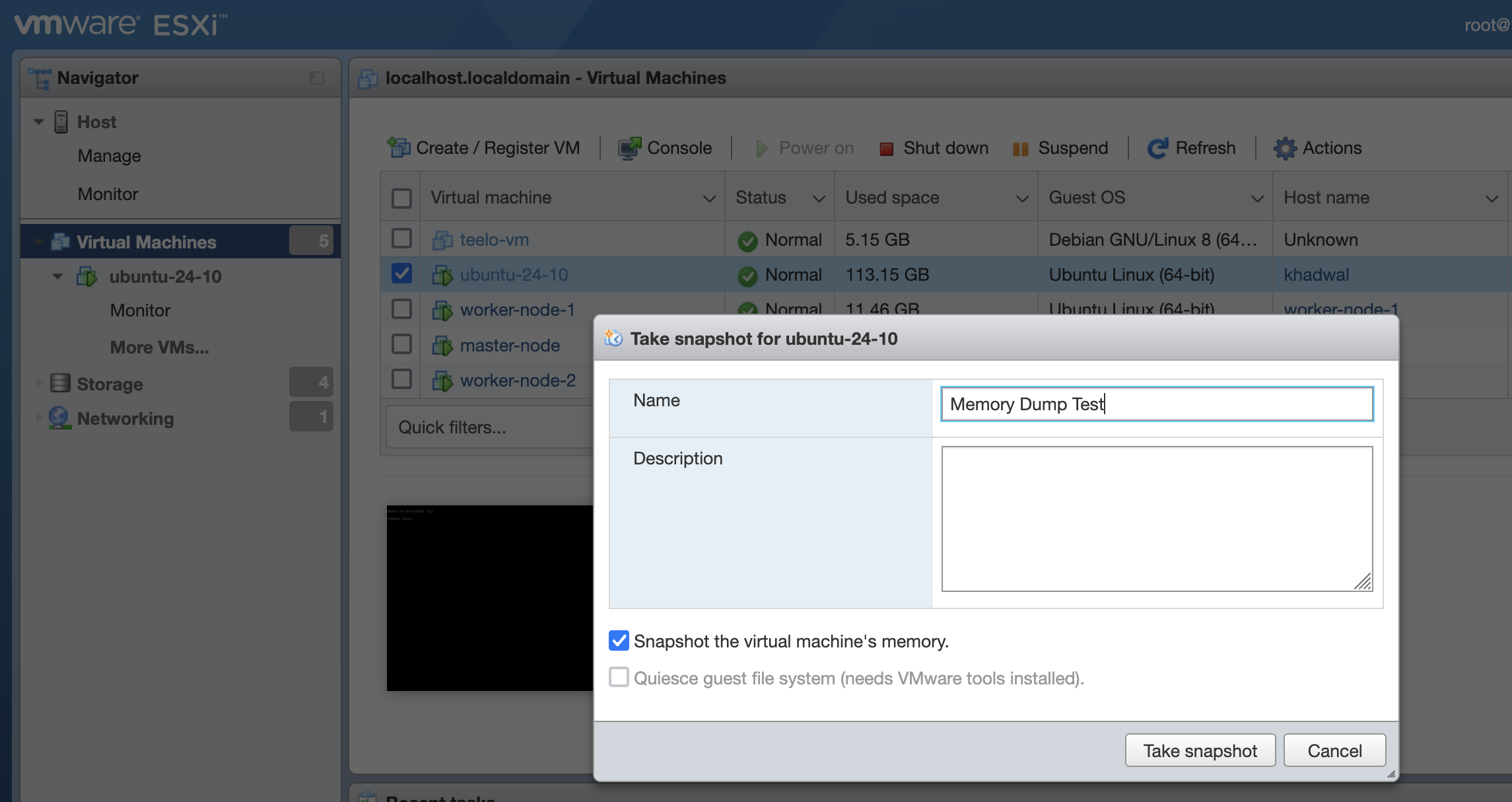
Taking a VMware Snapshot
-
In VMware ESXi/vSphere:
- Select VM > Right Click > Snapshots > Take Snapshot > Check (Snapshot the virtual machine’s memory)
Locating the Snapshot Files
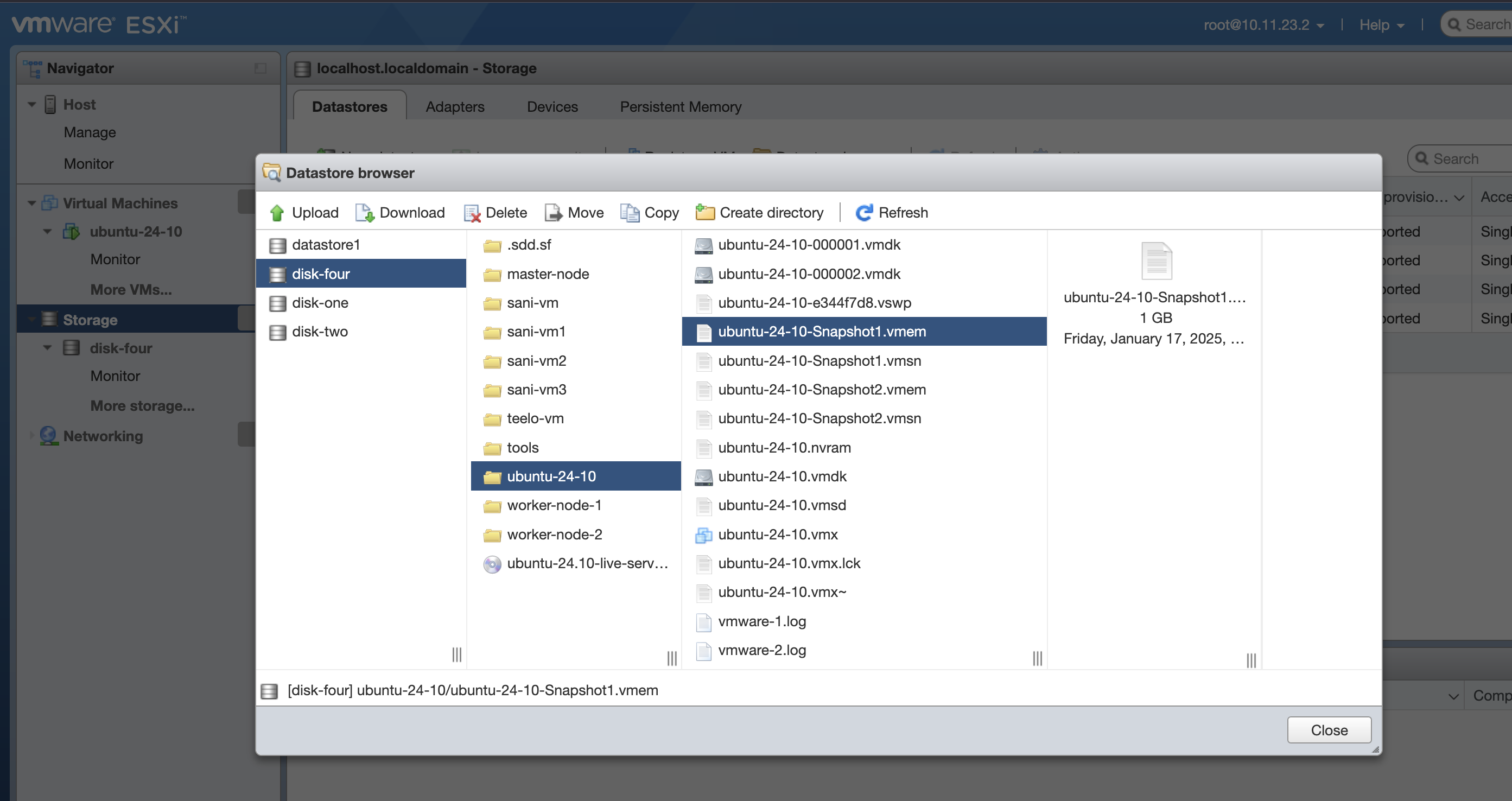
Option 1: Using the ESXi Datastore Browser
- Navigate to ESXi > Storage > Datastore Browser.
- Choose the disk where the VM is located.
- Select the VM
- Download the files with
.vmemand.vmsnextensions.
Option 2: Using SSH
- SSH into the ESXi host.
- Navigate to the VM’s directory:
cd /vmfs/volumes/{datastore_name}/{vm_name}
# Example:
cd /vmfs/volumes/disk-four/ubuntu-24-10
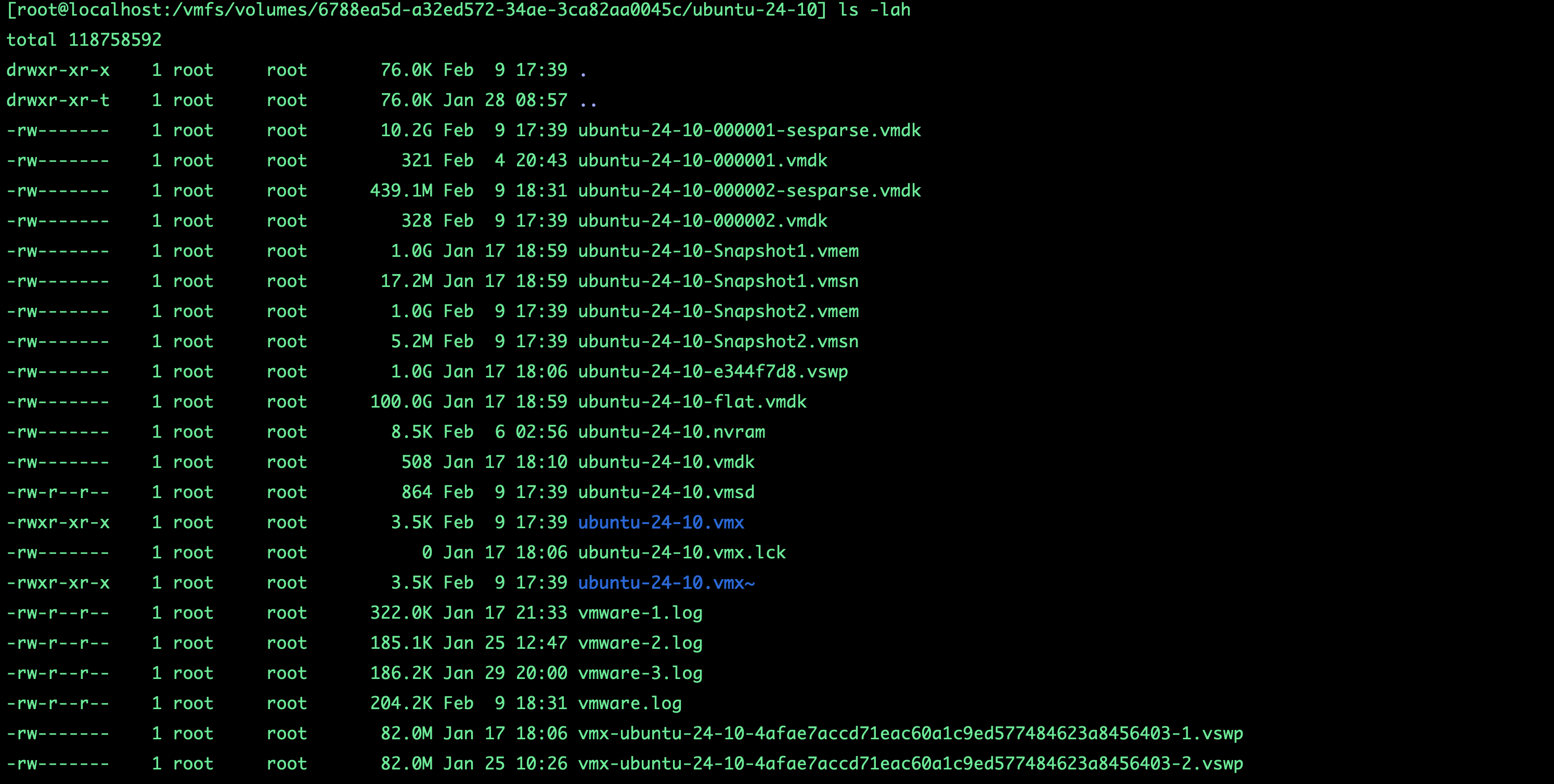
From the above, we are interested in two files:
.vmsn: A snapshot state file that contains the state of the VM, including memory, disk, and settings..vmem: A raw copy of the VM’s memory (RAM) at the time the snapshot was created.
The .vmem file can be quite large, as it contains the entire contents of the VM’s RAM. In the example above, the file is about 1GB.
Converting a VMware Snapshot to a Memory Dump
To convert a VMware snapshot into a memory dump, we use vmss2core.
What is vmss2core?
vmss2core is a utility provided by VMware that converts VMware snapshot files (.vmsn or .vmss) and memory files (.vmem) into a core dump format (e.g., .dmp or .core). This tool is particularly useful for debugging and analyzing VMs that have been paused, suspended, or snapshotted.
Locating vmss2core
If you have VMware Workstation or VMware Fusion installed, you can find vmss2core here:
Windows (32-bit): C:\Program Files\VMware\VMware Workstation\
Windows (64-bit): C:\Program Files (x86)\VMware\VMware Workstation\
Mac OS: /Library/Application Support/VMware Fusion/
If you can’t find it or don’t have it installed, you can download it for Windows, macOS, or Linux from:
Converting to a Memory Dump Based on OS
For Linux:
vmss2core -N vm_name.vmsn
For Windows 8 or Windows Server 2012 and later:
vmss2core -W8 vm_name.vmsn vm_name.vmem
For Windows 7 or Windows Server 2008 and older:
vmss2core -W vm_name.vmsn vm_name.vmem
Converting the Snapshot Image
vmss2core -N ubuntu-24-10-Snapshot1.vmsn ubuntu-24-10-Snapshot1.vmem
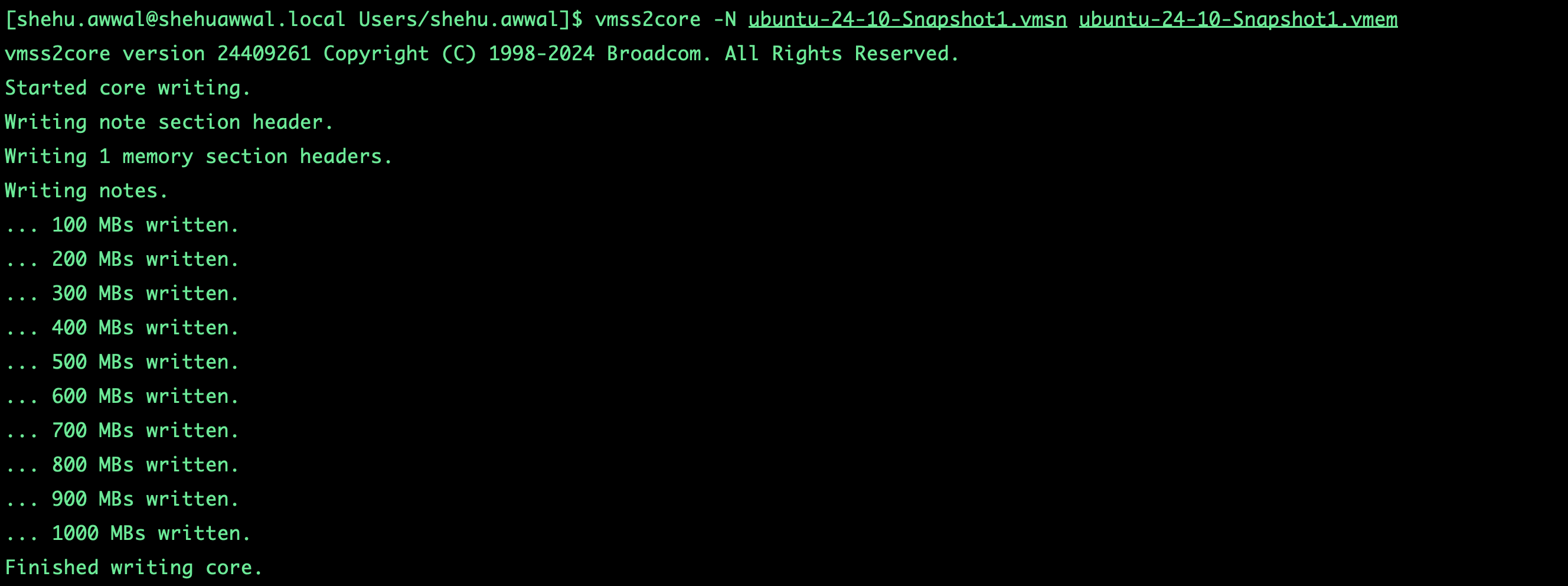
After it finishes, you will see a file named vmss.core.
At this point, we have a memory dump that we can analyze using tools like Volatility3, WinDbg, Rekall, etc., depending on the operating system of the dump file.
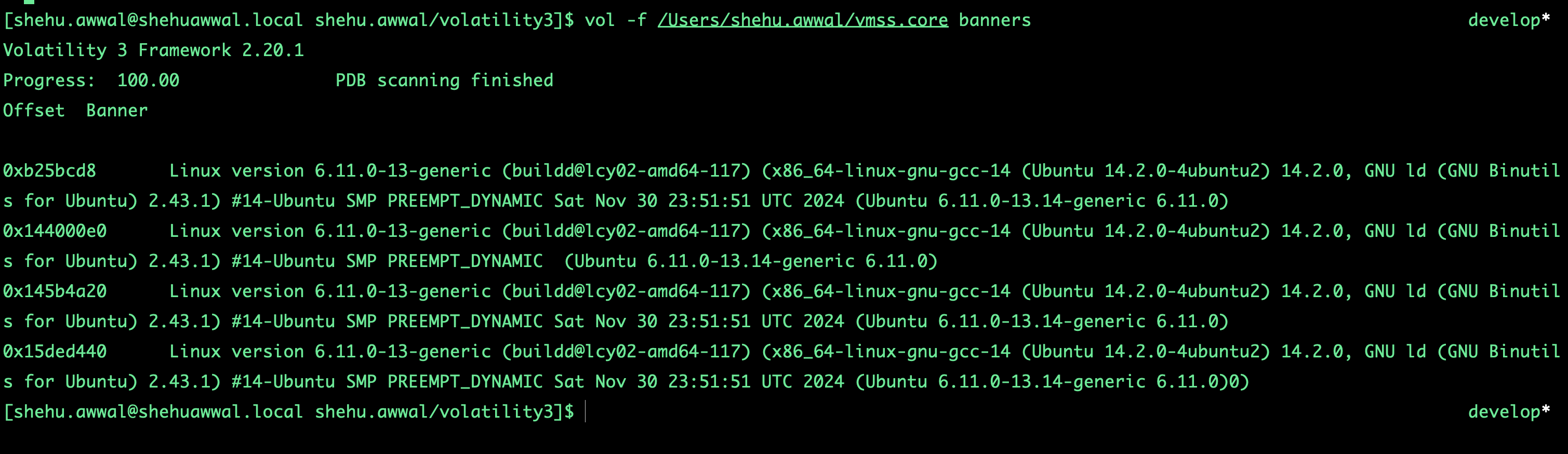
Analyzing the vmss.core Dump File with Volatility3
You can install Volatility3 using pip3 or uv:
uv pip install --system volatility3
# or
pip install volatility3
To analyze the memory dump, use the following command:
vol -f /Users/shehu.awwal/vmss.core banners
Converting a VMware snapshot to a memory dump is essential for forensic analysis and malware investigations. Memory dumps provide invaluable insights into the state of a VM at a specific moment, allowing analysts to detect hidden malware, analyze system behavior, and troubleshoot critical issues. By following this guide, you can efficiently extract and analyze VM memory snapshots, enhancing your investigative capabilities.
Comments: